How can I configure my virtual machine to permit unrestricted incoming and outgoing traffic?
To enable all incoming and outgoing traffic for your virtual machine, configure security rules to permit inbound and outbound traffic on all ports and IP addresses.
To enable all incoming and outgoing traffic for your virtual machine, configure security rules to permit inbound and outbound traffic on all ports and IP addresses.
Security rules for your virtual machines can be created using two different methods: the Hyperstack platform and Infrahub API.
Hyperstack
How to create security rules to permit unrestricted incoming and outgoing traffic.
These instructions guide you through the process of creating security rules that allow all incoming traffic from any port and any IP address to your virtual machine using the Hyperstack platform:
-
While viewing the Virtual Machine's Details page, click the "Firewall" section in the sidebar to manage its security rules:

-
Click "Add New Inbound Rule" to create a security rule for incoming traffic.
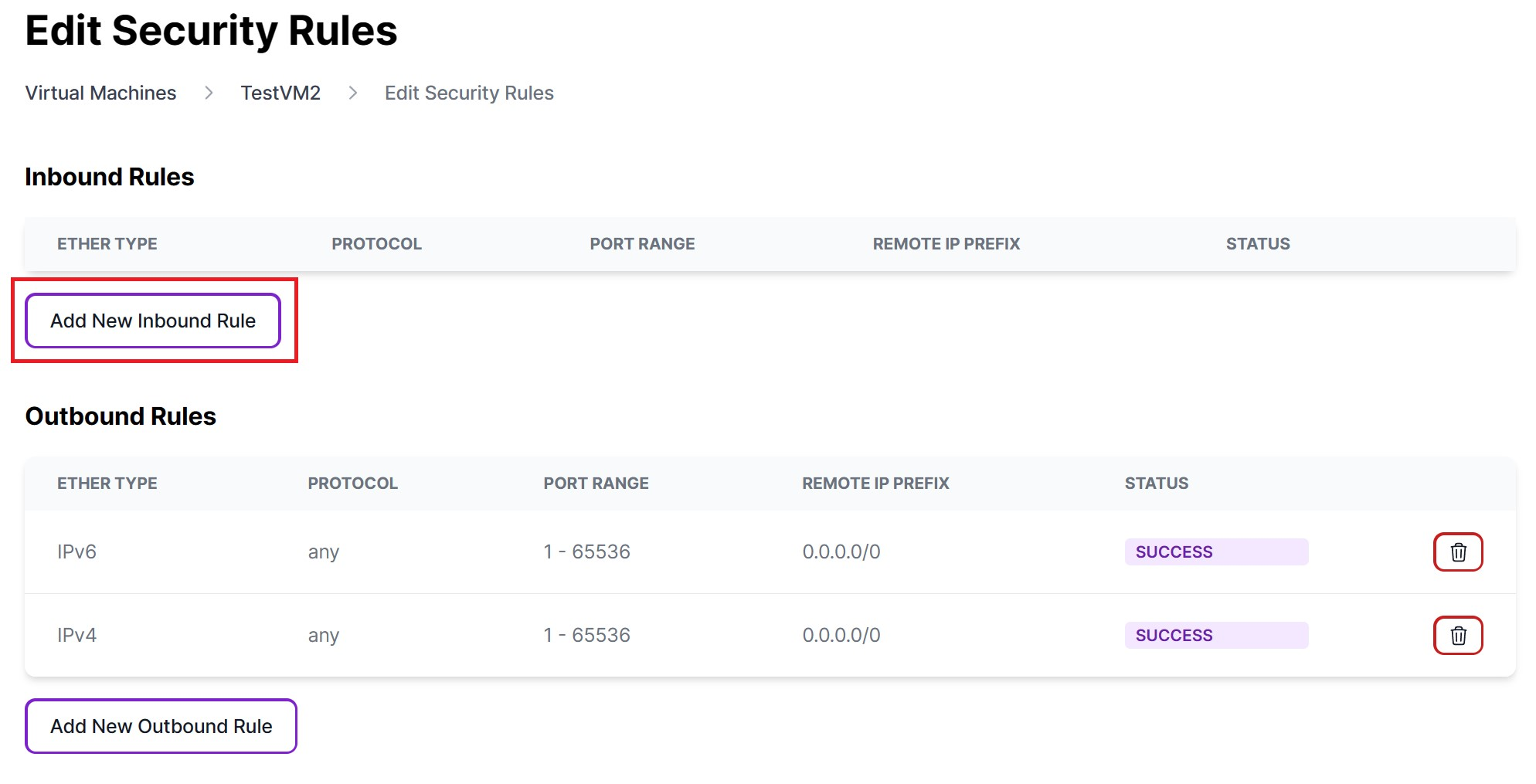
-
Complete the fields as specified below to enable all incoming traffic on all ports from any IP address.
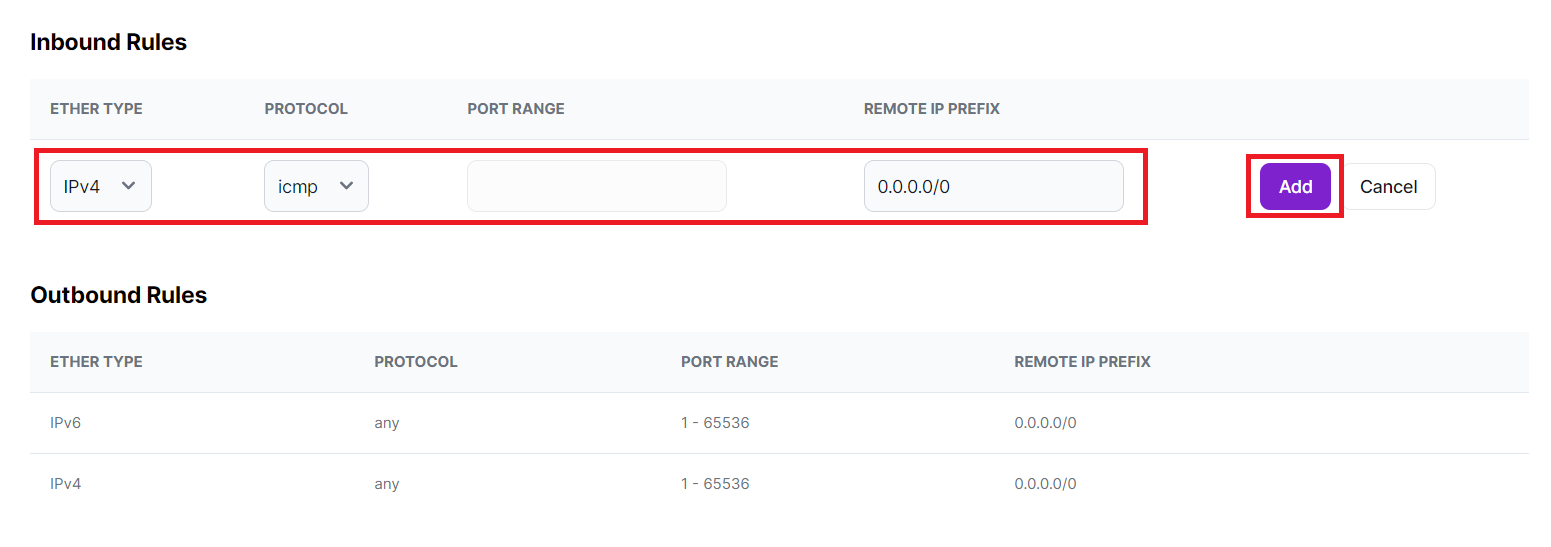
Field Name Field Input ETHER TYPE Leave as default (usually IPv4) PROTOCOL Select "icmp" (Internet Control Message Protocol) PORT RANGE This field is left empty, permitting traffic from all ports. REMOTE IP PREFIX Use "0.0.0.0/0" to allow traffic from any source IP address. -
Click "Add", to create a security rule enabling all incoming traffic.
-
Now that you've created a security rule allowing all incoming traffic, follow the same steps to establish a rule for outgoing traffic. Click "Add New Outbound Rule" to configure a security rule for outgoing traffic.
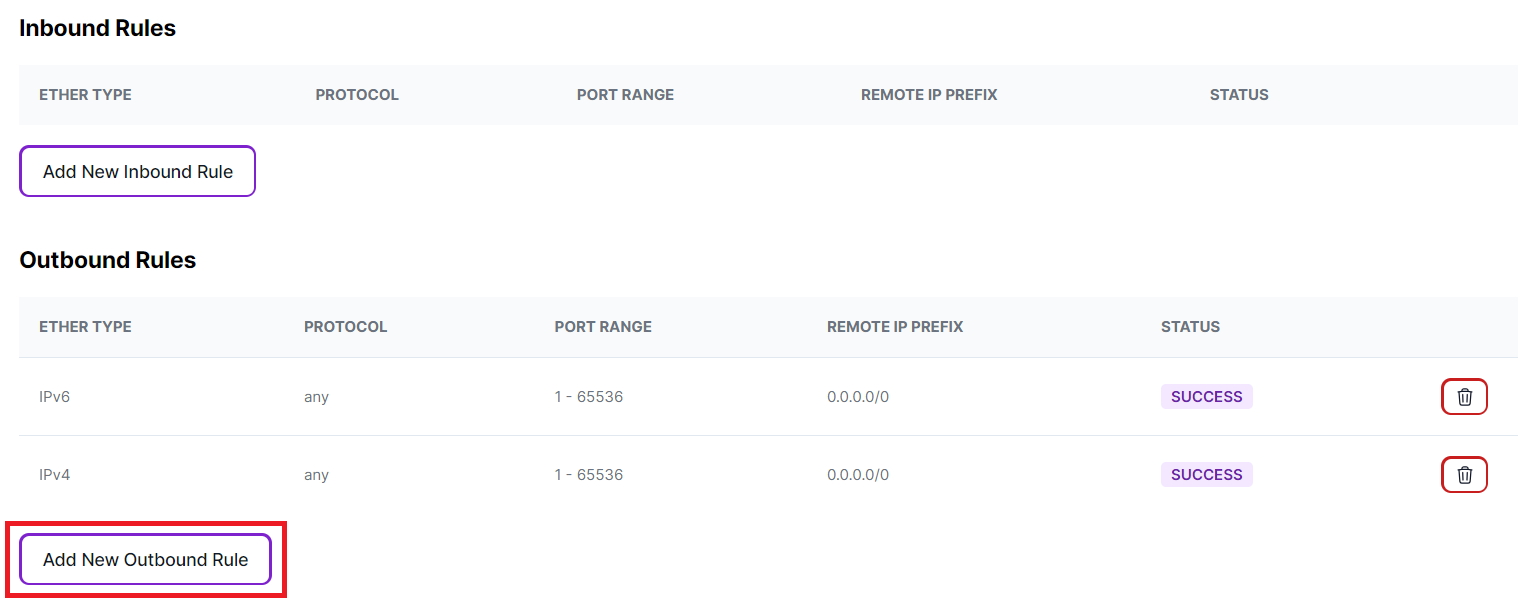
-
Complete the fields as specified below to enable all outgoing traffic on all ports to any IP address.
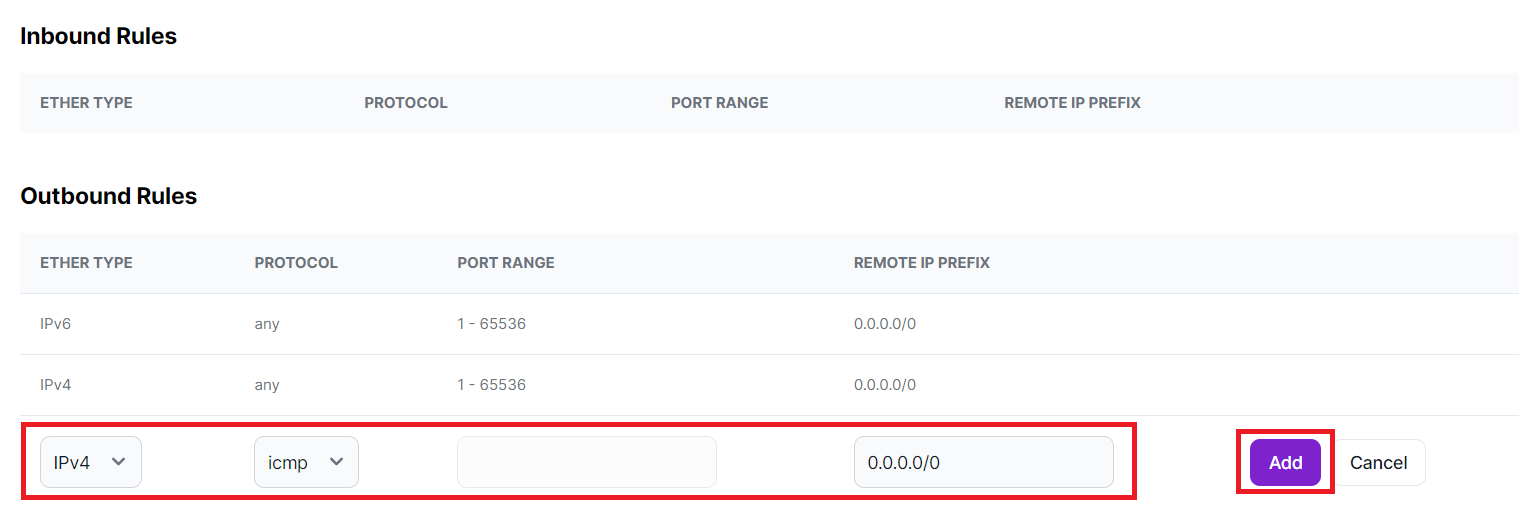
Field Name Field Input ETHER TYPE Leave as default (usually IPv4) PROTOCOL Select "icmp" (Internet Control Message Protocol) PORT RANGE This field is left empty, permitting traffic to all ports. REMOTE IP PREFIX Use "0.0.0.0/0" to allow traffic to any IP address. -
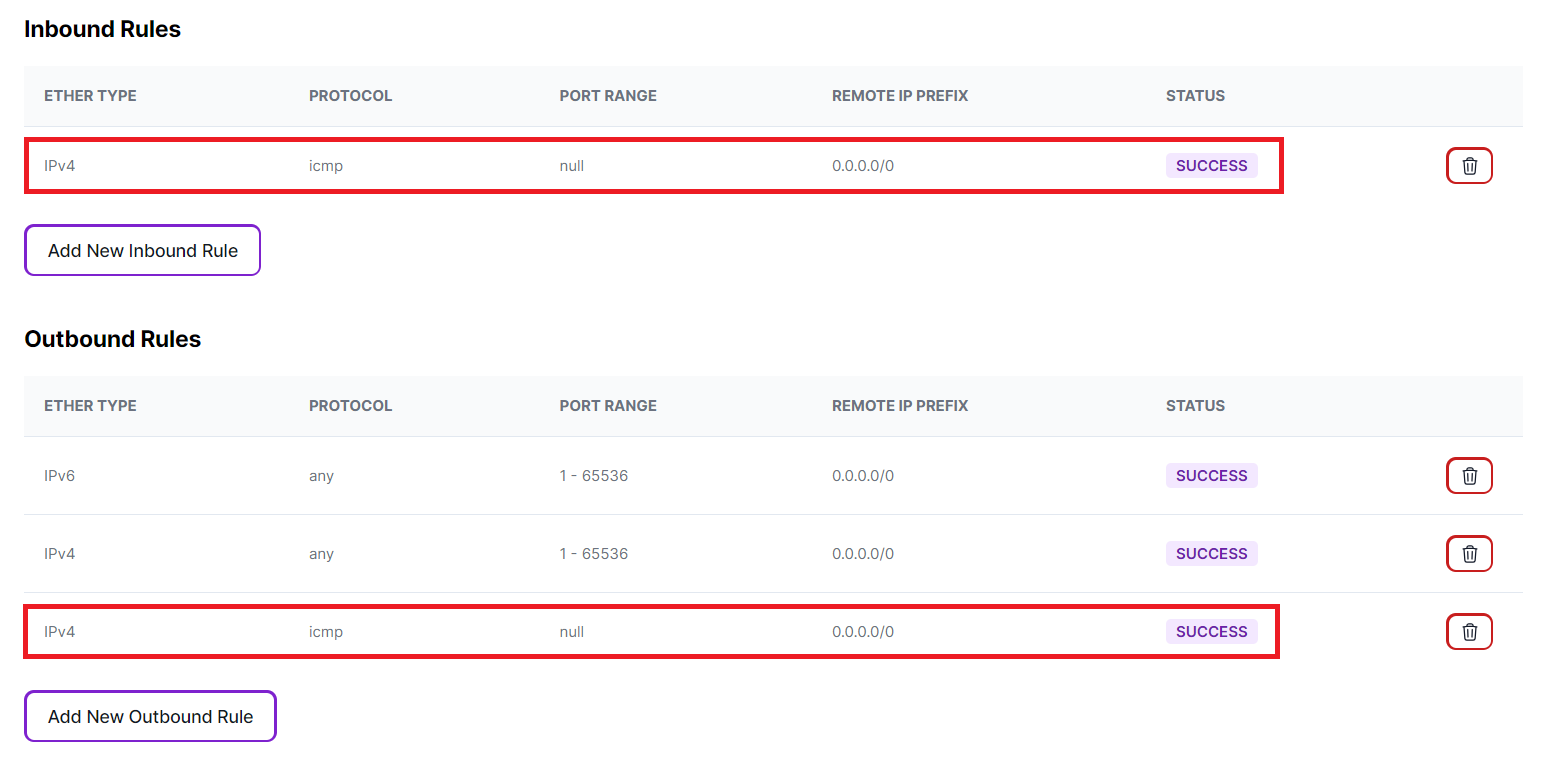
Your inbound and outbound security rules should appear as follows:
Infrahub API
These instructions walk you through the process of creating security rules that allow all incoming and outgoing traffic from any port and any IP address to your virtual machine using the Infrahub API.
1. Create an inbound rule via the Infrahub API
Path parameters
Include the integer ID of the virtual machine that this security rule is being attached to in the path of the request as follows: /core/virtual-machines/{VM ID HERE}/sg-rules
Request body parameters
Complete the request body with the following fields and values.
| Field Name | Field Input |
|---|---|
| direction | "ingress" to designate that the security rule is for incoming traffic. |
| protocol | Select "icmp" (Internet Control Message Protocol). |
| ethertype | "IPv4". |
| remote_ip_prefix | Use "0.0.0.0/0" to allow traffic from any source IP address. |
curl -X POST "https://infrahub-api.nexgencloud.com/v1/core/virtual-machines/123/sg-rules" \
-H "accept: application/json"\
-H "content-type: application/json" \
-H "api_key: YOUR API KEY" \
-d '{
"direction": "ingress",
"protocol": "icmp",
"ethertype": "IPv4",
"remote_ip_prefix": "0.0.0.0/0"
}'
To authenticate Infrahub API requests, add an authorization header to your API request that contains an API Key as follows:
-H "api_key: YOUR API KEY"
Returns
Returns the status of the security rule creation operation, along with the configuration details that were specified in the request body.
This response indicates the successful addition of a security rule that will permit all incoming traffic (ingress) from all ports, using the ICMP protocol and Ethernet type "IPv4" for the virtual machine with the ID "123".
{
"status": true,
"message": "Security Rule created successfully",
"security_rule": {
"id": 2296,
"direction": "ingress",
"protocol": "icmp",
"port_range_min": null,
"port_range_max": null,
"ethertype": "IPv4",
"remote_ip_prefix": "0.0.0.0/0",
"status": "pending",
"created_at": "2023-11-24T19:59:01"
}
}
2. Create an outbound rule via the Infrahub API
Path parameters
Include the integer ID of the virtual machine that this security rule is being attached to in the path of the request as follows: /core/virtual-machines/{VM ID HERE}/sg-rules
Request body parameters
Complete the request body with the following fields and values.
| Field Name | Field Input |
|---|---|
| direction | "egress" to designate that the security rule is for outgoing traffic. |
| protocol | Select "icmp" (Internet Control Message Protocol). |
| ethertype | "IPv4". |
| remote_ip_prefix | Use "0.0.0.0/0" to allow traffic to any IP address. |
curl -X POST "https://infrahub-api.nexgencloud.com/v1/core/virtual-machines/123/sg-rules" \
-H "accept: application/json"\
-H "content-type: application/json" \
-H "api_key: YOUR API KEY" \
-d '{
"direction": "egress",
"protocol": "icmp",
"ethertype": "IPv4",
"remote_ip_prefix": "0.0.0.0/0"
}'
Returns
Returns the status of the security rule creation operation, along with the configuration details that were specified in the request body.
This response indicates the successful addition of a security rule that will permit all outgoing traffic (egress) to all ports, using the ICMP protocol and Ethernet type "IPv4" for the virtual machine with the ID "123".
{
"status": true,
"message": "Security Rule created successfully",
"security_rule": {
"id": 2297,
"direction": "egress",
"protocol": "icmp",
"port_range_min": null,
"port_range_max": null,
"ethertype": "IPv4",
"remote_ip_prefix": "0.0.0.0/0",
"status": "pending",
"created_at": "2023-11-24T20:33:46"
}
}
Keep in mind that allowing all traffic might pose security risks, so use this configuration carefully and consider the specific requirements of your use case.
References:
For further assistance, don't hesitate to reach out to us at:
Support Email: support@hyperstack.cloud
Sales Contact: sales@hyperstack.cloud
Phone: +44 (0) 203 475 3402